What is Cryptography?
Cryptography is a technique or method of applying mathematical concepts to a piece of information given some rules in order to secure the information and keep it secure from intruders. The information will be secured by the sender and can only be extracted by the receiver. Thus, it is a practice in order to bring secure communication between devices that may have the threat of getting information stolen by any third-body intrusion.
If we tend to separate the words Cryptography, it is divided as crypt meaning “to keep secret” or “hide” and graphy meaning “writing”. It can be seen that it can be simply termed as hidden writing or written information which is hidden.
Let's understand the same using a story:
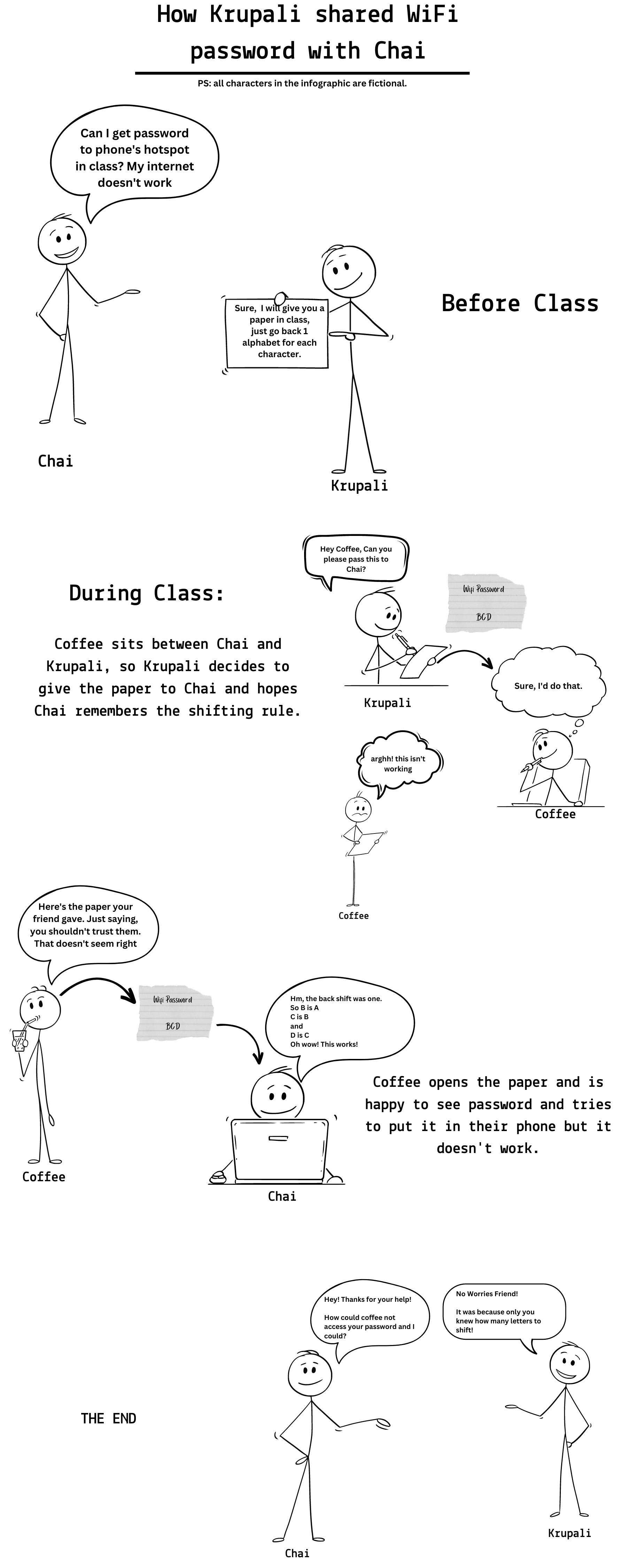
The story we see above is a simple example of an encryption technique also known as Caesar cipher. We just shifted the letters and only the sender and receiver knew what amount of shift was done, making it inaccessible for any intruder to use your message in any way.
In the above example, the original WiFi password was "ABC" which was encrypted by shifting the letters by adding one to the number. Suppose, A is one (as counted in the alphabet), so we added one to it, (1+1) and thus it became two, the letter corresponding to two is B in the alphabet and thus we get B instead of A. Similarly, we made changes for B and C in the original password. After the shift, the text became "BCD" which was passed along. This changed text is also known as Cipher Text.
Thus, we can say that Cryptography helps in making communication hidden or private.
The process we saw above is also called Encryption-Decryption. It is one of the processes used in Cryptography to hide the message to be sent.
Encryption and Decryption:
As we learned above, it was a simple example of the Encryption and Decryption process which is extremely helpful in Cryptography.
Encryption is a process of applying logic and mathematical function so that an informative text appears as a random text which does not imply any meaning. It is a process where a cryptographic key is used to make the message unreadable.
Key: The key used in the process of encryption and decryption is a set of mathematical values upon which the sender and receiver would have agreed. The keys are of two types, Public Keys and Private Keys. As the name suggests, the public keys are made public and private keys remain hidden from the world except for an individual.
We will learn more about their uses in upcoming sections and following blogs.
To make the random text readable again, we use Decryption. It is a process of making the unreadable text to a readable and meaningful form again with the help of the key and mathematical functions.

Features of Cryptography:
Why exactly do we need to hide our messages and what is the need of Cryptography? There are some essential features provided by Cryptography that will help to better understand how exactly it is useful.
Confidentiality: This feature of confidentiality ensures that the information is inaccessible to anyone except the receiver. Thus, privacy is maintained when cryptography is involved.
Authentication: The feature of authentication ensures the identities of the sender and receiver during the process of information sharing. Identities are confirmed when transmission occurs to ensure that the right person is sharing information and the targeted person is getting the information.
Integrity: This feature ensures that the message is not changed or tampered with while passing through the channel. The alteration can be done only by the sender or receiver.
Non-Repudiation: Once information is shared through the channel, the sender cannot deny sharing or sending the information and similarly the receiver cannot have their involvement in the communication i.e they have not received the message.
Next, let's learn how we have come so far with automated cryptography right from when it was in the raw, inscribed format.
History of Cryptography:
Cryptography isn't a modern technique, it has traveled through centuries - changing and getting updates with new methodologies. The first evidence of cryptography can be found dating back to 1900 BC Egypt. The messages found here were hidden not to pass on any secret information but for fun and amusement. These inscriptions are hieroglyphs that are formed by combining logos, syllables and alphabets.

As the form of learning and writing evolved, cryptography started being used in the military. A notable instance of this is the Scytale of Sparta (in Ancient Greece) which served a purpose for the Spartan military. The tools used for this cryptography were wound tapes and sticks.
Julius Caesar in 100 BC formed the encryption technique - Caesar cipher that used the method of alphabet shifting. This form was used to convey secret messages on the war front.
As science advanced, so did cryptographic technology, leading to the realization of the need for new terms. According to D. Kahn, modern cryptography originated in Arabs. The book of Al-Khalil's "Book of Cryptographic Messages" was the first to use mathematical terms such as permutations and combinations, listing all possible Arabic words with and without vowels. Recently discovered manuscripts report that Al-Kindi, an Arab mathematician and polymath in the 9th century, used frequency analysis to build cipher text and wrote a book on cryptography titled "Rislah fi Istikharaj al-Mu'amma". These ciphers are still used to create puzzles today.

In the 2000-year-old Kamasutra of Vatsyayana, ancient India displayed evidence of using cryptography through the ciphers Kauitiliyam and Mulavediya. Kautalya's Arthshashtra, a renowned work on statecraft, also mentioned the use of "secret writing" in assigning tasks to spies in India's espionage service.
Several following iterations of the ciphers dating to the present are as follows:
Leon Battista Alberti is believed to have invented the first cipher device, which was automatic and used a wheel.
Blaise de Vigenere invented the Vigenere cipher, which is a polyalphabetic cipher and is considered one of the most interesting cipher devices. It is a modification of the Caesar cipher.
Several sophisticated cipher machines were invented until the early 20th century.
During World War II, German soldiers used the Enigma machine to transfer crucial data among Nazi soldiers. The Enigma machine was invented by German engineer Arthur Scherbius at the end of World War I with the purpose of protecting commercial, diplomatic, and military communication.
The Enigma machine was one of the finest rotor machines among the others at that time.
Ancient humans have given us the boon of hiding messages and as science and technology evolved, we're seen tremendous evolution in cryptographic methods. Let's now move on to some modern cryptography techniques.
Types of Cryptography:
To understand the types of cryptography, we will be mainly focusing on encryption (as explained above)
Symmetric Key Cryptography or Secret Key Cryptography
Asymmetric Key Cryptography or Public Key Cryptography
Hash Functions

- Symmetric Key Cryptography: In symmetric key cryptography, the same key is used for encryption and decryption. In symmetric key cryptography, the sender and receiver have access to the same key (shared over a secure channel) used for communication. Examples of symmetric-key cryptography algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Blowfish.

Asymmetric Key Cryptography: In asymmetric key cryptography, there are two keys: private and public keys. As per the usage, (i.e encrypting an information or working on a digital signature) one of the keys will be used for encryption and the other one is used for decryption. It is important to see that the private key is personal for each entity and cannot be shared with anyone else. The public key, as the name suggests, can be shared with anyone but the private key must be secret.

Hash Functions: Hash functions are one-way mathematical functions that transform input data into a fixed-size output called a hash or message digest. Hash functions are used for data integrity, digital signatures, and password storage.

Some other types of cryptographical techniques are:
Quantum Cryptography: Quantum cryptography uses the principles of quantum mechanics to create unbreakable encryption keys. Quantum cryptography is still in the experimental stage and not yet widely used.
Steganography: Steganography is the practice of hiding information within other information, such as an image or audio file. Steganography is used to conceal the existence of secret information.
Homomorphic Encryption: Homomorphic encryption allows computations to be performed on encrypted data without decrypting it first. Homomorphic encryption has potential applications in cloud computing and secure data sharing.
Applications of Cryptography:
Cryptography is used in multiple sectors in order to provide security.
Secure communication: Cryptography is used to secure communication over public networks like the internet, making it difficult for unauthorized individuals to access or intercept sensitive information. Secure communication is essential in industries such as finance, healthcare, and government.
E-commerce: Cryptography is used to secure online transactions, including online banking, e-commerce, and electronic voting. The use of cryptography ensures that the transaction is secure and that the data is protected from unauthorized access.
Password protection: Cryptography is used to store passwords securely. When users create a password, it is encrypted and stored in a secure database.
Digital signatures: Digital signatures are commonly used in legal, financial, and government documents to ensure that the document has not been altered or modified in any way.
VPNs: Cryptography is used in Virtual Private Networks (VPNs) to create a secure connection between two endpoints, such as a user's computer and a remote server. The use of cryptography ensures that the data exchanged between the endpoints is secure and protected from unauthorized access.
Data storage: Cryptography is used to protect data stored on hard drives, USB drives, and other digital storage devices. Data encryption ensures that the data cannot be accessed by unauthorized individuals, even if the storage device is lost or stolen.
Disadvantages of Cryptography:
So far, we have seen the advantages of cryptography and its application but flipping the coin, we have the other side.
Sometimes a highly encrypted message becomes difficult to decrypt even with authenticated users which might lead to problems.
Key management becomes extremely difficult as the key needs to be a secret and has to be shared through secure material and has to be kept safe.
The encryption process can become computationally expensive and the performance can deteriorate.
The security of cryptography is ensured by the complexity of the mathematical functions and logic but they are vulnerable to attacks as well.
References:
https://www.tutorialspoint.com/cryptography/benefits_and_drawbacks.htm
https://www.analyticssteps.com/blogs/characteristics-types-and-applications-cryptography
About the Author:
I am Krupali | Chai - a content writer and a person who enjoys talking to people and discussing everything related to tech, music and books. When not writing, you can find me hanging out on Twitter or Discord.